| Role Availability | Read-Only | Investigator | Analyst | Manager |
- All assets must be visible to Tenable.
- Public assets should use the Tenable Cloud Scanner.
- Private assets require a locally installed Nessus scanner.
- Review and validate asset credentials before running authenticated scans.
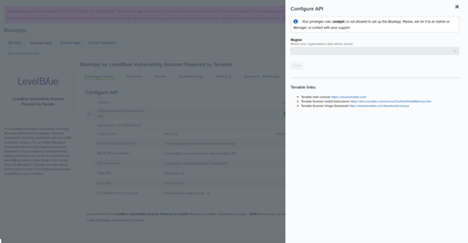
- Navigate to Data Sources and open the Available BlueApps tab.
- Filter by Scanner, then select LevelBlue Vulnerability Scanner powered by Tenable.
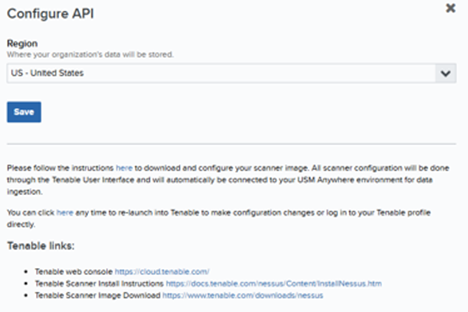
- Click Configure API, and then select the region where configuration data will be stored.
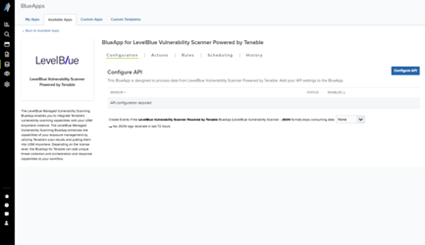
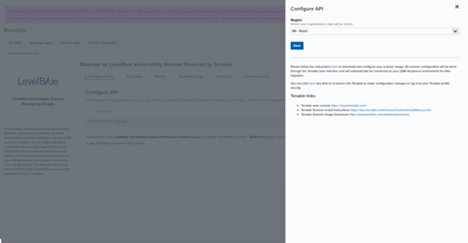
- Click Save.
Note: Only users with the Manager role can perform this configuration.
- Once the configuration is completed, you will receive an email confirmation.
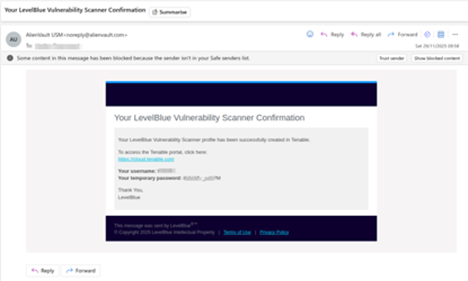
- Log in to the Tenable portal at https://cloud.tenable.com using the temporary credentials provided.
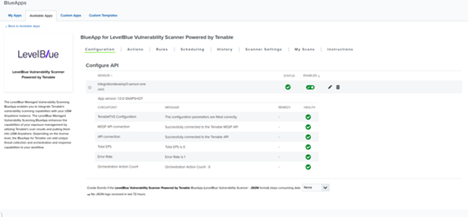
- In the Authorize Apps tab of the LevelBlue Vulnerability Scanner page, open Scanner Settings, and then select a default scan template.
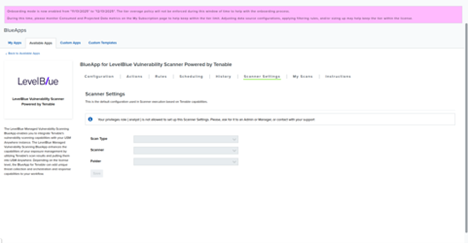
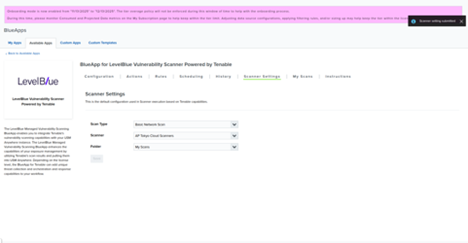
Note: Only Manager-role users can configure default scan templates.
- Navigate to assets or asset groups and run scans as usual.
- Open the Scheduling tab to configure periodic scans.
Before running authenticated scans, verify the following:
- Assets are visible to Tenable Cloud or have a Nessus scanner installed.
- Credentials are valid and assigned to the correct assets.
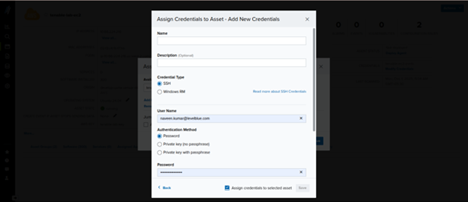
- Add new credentials
- Assign credentials to assets
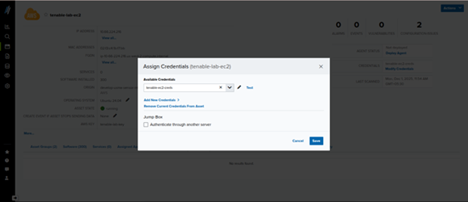
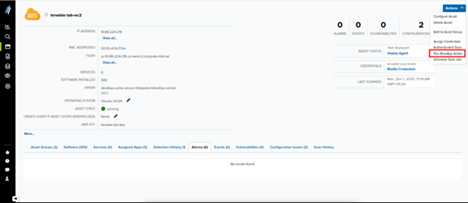
- Open the Asset page.
- Confirm credentials are assigned.
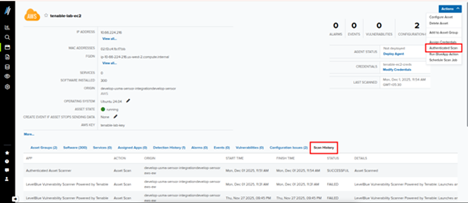
- Click Actions.
- Select Authenticated Scan.
- Open the Asset Group page.
- Confirm all assets in the group have credentials assigned.
- Click Actions.
- Select Authenticated Scan.
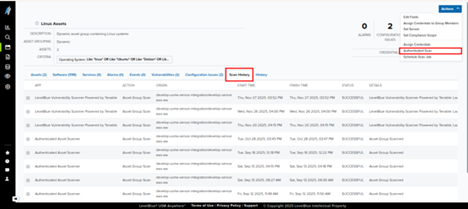
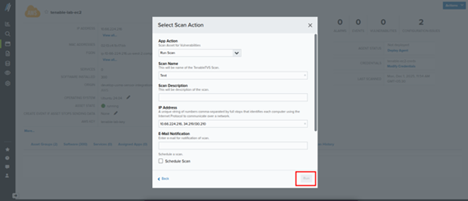
- From the Actions menu, select Run BlueApp Action.
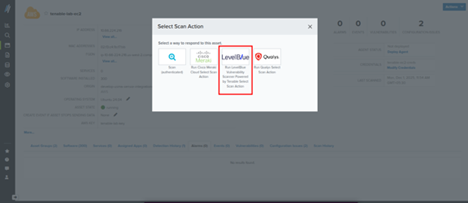
- Choose Run LevelBlue Vulnerability Scanner powered by Tenable.
- Select Run Scan.
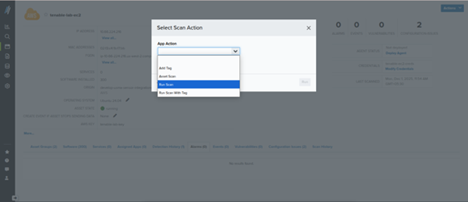
- Click Run.
https://docs.levelblue.com/documentation/usm-anywhere/user-guide/vulnerability-assessment/credentials. Download a Scan Result File
- Open the Asset or Asset Group page.
- Select the Scan History tab.
- Locate the Scan File column.
- Click the scan entry to download the file.
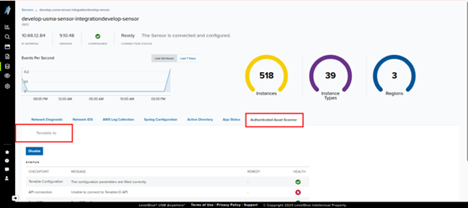
https://docs.levelblue.com/documentation/usm-anywhere/user-guide/vulnerability-assessment/credentials. Review Authenticated Scanner Status in a Sensor
- Navigate to Sensors.
- Select the sensor to review.
- Open the Authenticated Scanner tab.
- Download the Nessus scanner from: https://www.tenable.com/downloads/nessus.
- Follow the installation guide: https://docs.tenable.com/nessus/Content/InstallNessus.htm When prompted, select Link to another Tenable product.
- Link the scanner to your Tenable portal using these instructions: https://docs.tenable.com/vulnerability-management/Content/Settings/Sensors/LinkaSensor.htm.
- https://docs.tenable.com/vulnerability-management/Content/Scans/ScanBestPractices.htm
- https://docs.tenable.com/vulnerability-management/Content/Scans/Credentials.htm
- Do not configure the LevelBlue Vulnerability Scanner on more than one sensor within the same LevelBlue USM domain. Doing so can cause scan and result errors.
- The Tenable license supports unlimited endpoints but API is limited to 8192 endpoints per scan. If scanning more then 8192 endpoints, multiple scans will be required.
| Questions | Answers |
|---|---|
| Is LevelBlue Vulnerability Scanner replacing the Tenable.io BlueApp? | No. Tenable.io BlueApp uses a separate Tenable account and is not fully integrated with LevelBlue USM. Asset group scans, authenticated scans, and other native USMA workflows are only supported through LevelBlue Vulnerability Scanner. |
| Can LevelBlue Vulnerability Scanner coexist with Tenable.io BlueApp? | Yes, but this may result in duplicate security data. |
| Can I use jOVAL and LevelBlue Vulnerability Scanner at the same time? | No. Enabling LevelBlue Vulnerability Scanner disables the jOVAL scanner. |
| Will existing scheduled scans be preserved? | No. All custom scheduled scan jobs must be recreated in the USMA Scheduler. There is no automated migration. |
| Will existing asset credentials still work? | Yes. The credential manager remains unchanged. |
| Which scan actions are deprecated? | Debug scan actions for assets and asset groups. |
| Can I access scan results in the Tenable portal? | Yes, but it is optional. Scan results and vulnerabilities are imported into LevelBlue USM automatically. |
| How do I log in to the Tenable portal? | After initial configuration, you receive an email with the portal link, username, and password. Additional user accounts will need to be provisioned in the tenable portal. Important: Save your Tenable username. It is required for USMA Technical Support and is tied to your USMA domain. |
| Which user roles can configure the scanner and settings in LevelBlue USM? | Only users with the USMA Manager role. |
| What data regions are supported? | Australia, Brazil, Canada, European Union, India, Japan, Singapore, United Kingdom, and United States. |