You can watch the Conducting Security Analysis with LevelBlue USM Anywhere customer training webcast on-demand to learn how to leverage USM Anywhere to perform security analyst duties.
- On the left side of the page are the search and filters options. Use filters to delimit your search.
- At the top of the page, you can see any filters you have applied, and you have the option to create and select different views of the alarms.
- The main part of the page is the list of alarms, where each row describes an individual alarm. Click an alarm to open a summary view. See Viewing Alarm Details for more information. Each alarm includes a checkbox that you can use to select it. You can select all alarms in the same page by clicking the checkbox in the first column of the header row. You can also select all the alarms in the system. See Selecting Alarms in Alarm List View for more information.
Refreshing the Page
USM Anywhere gives you the option of refreshing the page automatically in a period of time that you can configure. There is an auto-refresh countdown that refreshes the page at a regular interval. The number inside the blue circle indicates the remaining time until the next refresh. See Select the Time for Auto-Refreshing the Alarms and Dashboard Pages to configure this interval. You can click the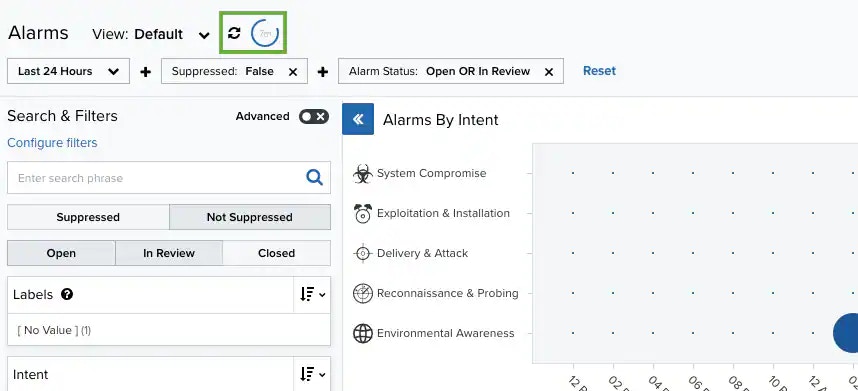
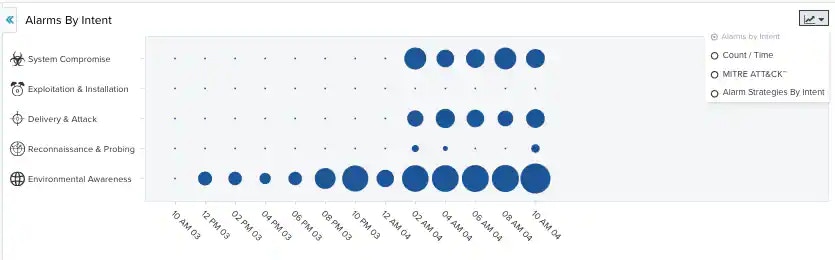
Alarm Summary Graph
The graph at the top of the Alarms page provides a graphical representation of alarms by intent. The blue circles indicate the number of times that an alarm in an intent occurred. A bigger circle indicates a higher number of alarms. You can hover over each of the circles to get the actual number of alarms per intent. In addition, clicking a blue circle displays a list of only the alarms corresponding to that circle. You can change the displayed period of time by clicking the Last 24 Hours filter. Alarms graphed by intent are sorted into five different categories, which are represented by the graphic icons in the display:- Delivery & Attack (
)
- Environmental Awareness (
)
- Exploitation & Installation (
)
- Reconnaissance & Probing (
)
- System Compromise (
)
 icon to change the alarms view.
icon to change the alarms view.
 icon accesses these options:
icon accesses these options:
- Alarms by Intent: This view is a bubble graph that provides a graphical representation of alarms by intent.
- Count/Time: This view provides a graphical representation of the number of alarms in a period of time.
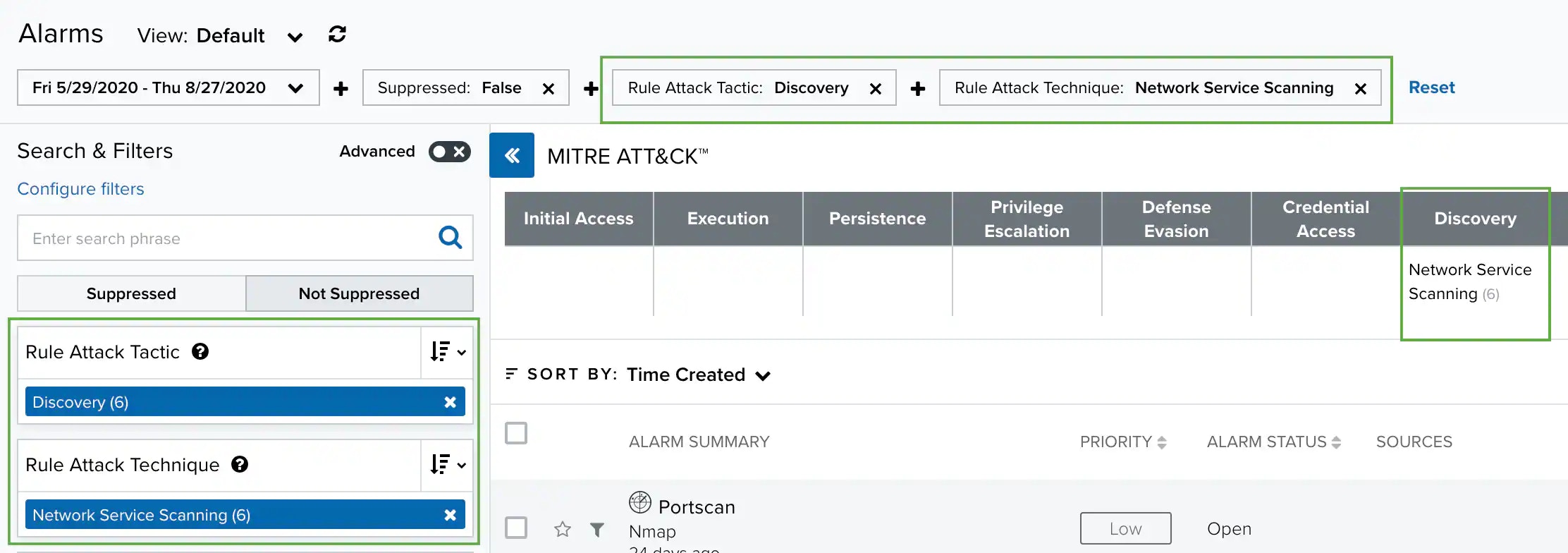
- MITRE ATT&CK: The MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a framework for understanding attackers’ behaviors and actions.
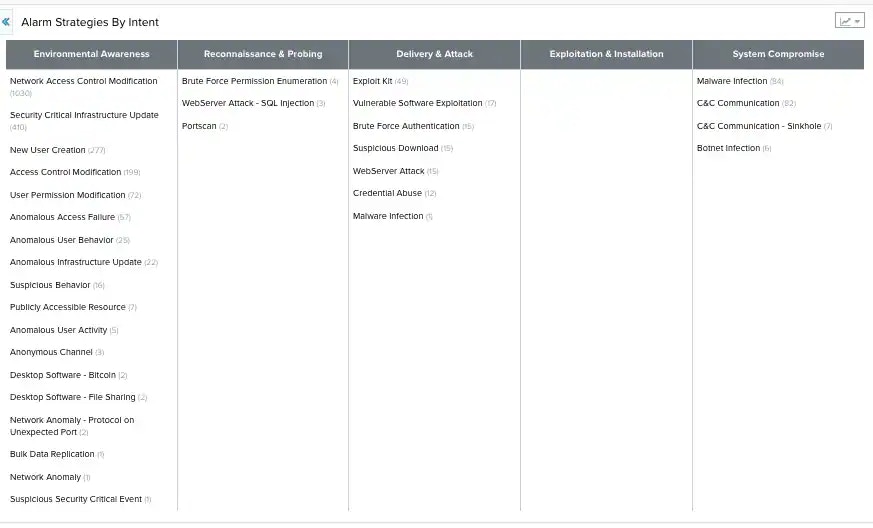
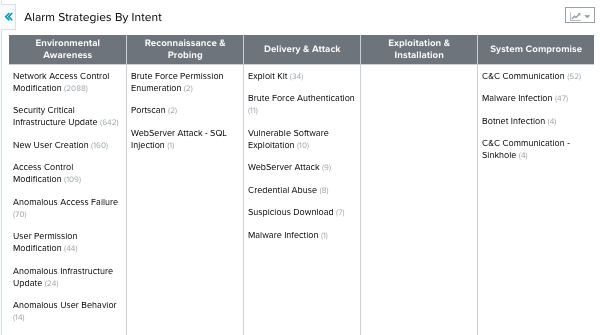
- Alarm Strategies by Intent: This view is a table that provides a representation of alarms strategies by intent.
The MITRE ATT&CK View
USM Anywhere and LevelBlue Labs™ Open Threat Exchange® (OTX™) include MITRE ATT&CK information. The alarms view incorporates a table with tactics and techniques to describe adversarial actions and behaviors. Techniques are specific actions an attacker might take and tactics are phases of attacker behavior. This view includes the alarms mapping to their corresponding ATT&CK techniques and helps you to understand the context and the scope of an attack. See MITRE ATT&CK for more information.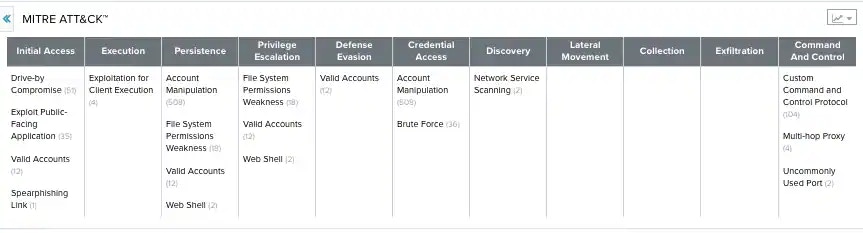
The Alarm Strategies by Intent View
The Alarm Strategies by Intent view displays a table that lists the purposes of the alarm. The table headers represent the intent of the alarms. The table rows display the strategies.