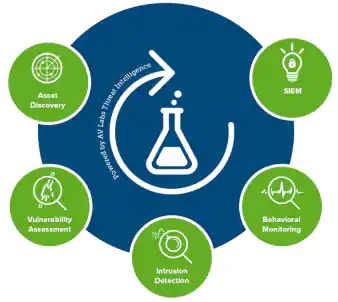
- Asset Discovery is an essential security capability of USM Anywhere, which discovers assets in your environment, detects changes in assets, and discovers malicious assets in the network.
- Vulnerability Assessment, which is done in authenticated state, identifies vulnerabilities or compliance by comparing the installed software on assets with a database of known vulnerabilities. Vulnerability scans can be performed manually or scheduled to be performed periodically.
- Intrusion Detection monitors network traffic for malicious activity, monitors system log messages, and monitors user activity. Intrusion detection for USM Anywhere consists of network-based intrusion detection (NIDS) components. HIDS can be used to spot problems on host endpoints, and can include file integrity monitoring, rootkit and registry checks. NIDS passive sniffing interfaces can analyze network payload data to monitor for potentially malicious activity.
- Behavioral Monitoring identifies suspicious behavior and potentially compromised systems. USM Anywhere provides continuous monitoring of services run by particular systems. Data used for behavioral monitoring and analysis is collected from network devices and user behavior. USM Anywhere has access to logs in the cloud (Azure: Monitor, AWS: CloudTrail, S3, ELB) and VMware logs.
- SIEM and Log Management correlates and analyzes security event data and respond. USM Anywhere SIEM draws intelligence from different sources including the LevelBlue Labs Threat Intelligence Subscription and OTX. Correlation rules, created by the Security Research Team, are used to identify patterns associated with malicious activity. OTX threat data provides IP reputation information and OTX pulses, which consist of Indicators of Compromise (IOCs) that identify a specific threat.