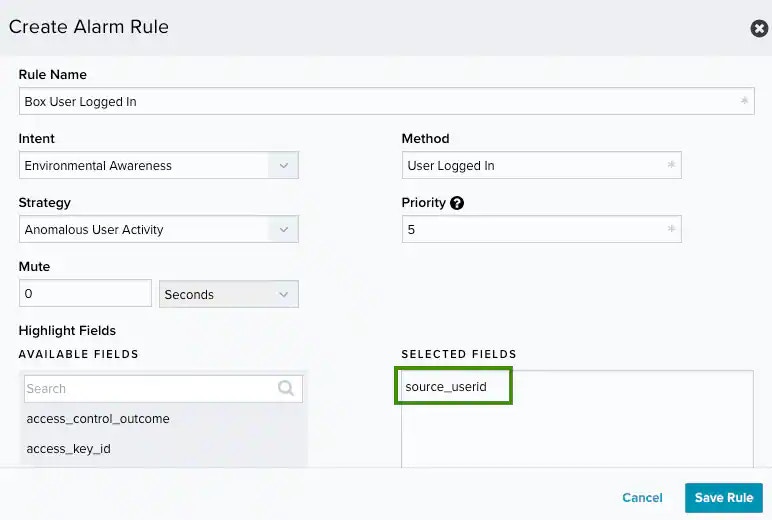
| Intent | Strategy | Method |
|---|---|---|
| System Compromise | Credential Abuse | Authentication to Box from a known malicious host |
| Ransomware Infection | Multiple uploads with known ransomware extension | |
| Ransomware decryption instructions file upload | ||
| Exploitation & Installation | Malware Infection | Executable downloaded from Box followed by malware activity |
| Delivery & Attack | Brute Force Authentication | Successful login after a brute-force attack |
| Password spraying against Box | ||
| Data Exfiltration | File sent to a known malicious host | |
| Known Malicious Infrastructure | Box application created from a known malicious host | |
| File shared from a known malicious host | ||
| Reconnaissance & Probing | Brute Force Authentication | Multiple login failures |
| Environmental Awareness | Access Control Modification | Two-factor authentication disabled |
| Account Manipulation | Multiple user accounts deleted | |
| Anomalous User Behavior | Admin login from an unknown device | |
| Credential Abuse | User login from two different countries in a short period | |
| Defense Evasion - Cover Tracks | User account created and deleted in short period | |
| Defense Evasion - Disabling Security Tools | Box security policy deleted | |
| Malware Infection | Box detected a malicious file upload | |
| Sensitive Data Disclosure | Box support access granted |