| Role Availability | Read-Only | Investigator | Analyst | Manager |
SIEM Section
security intelligence combines and correlates collected logs and other data to find patterns in network traffic and within activity.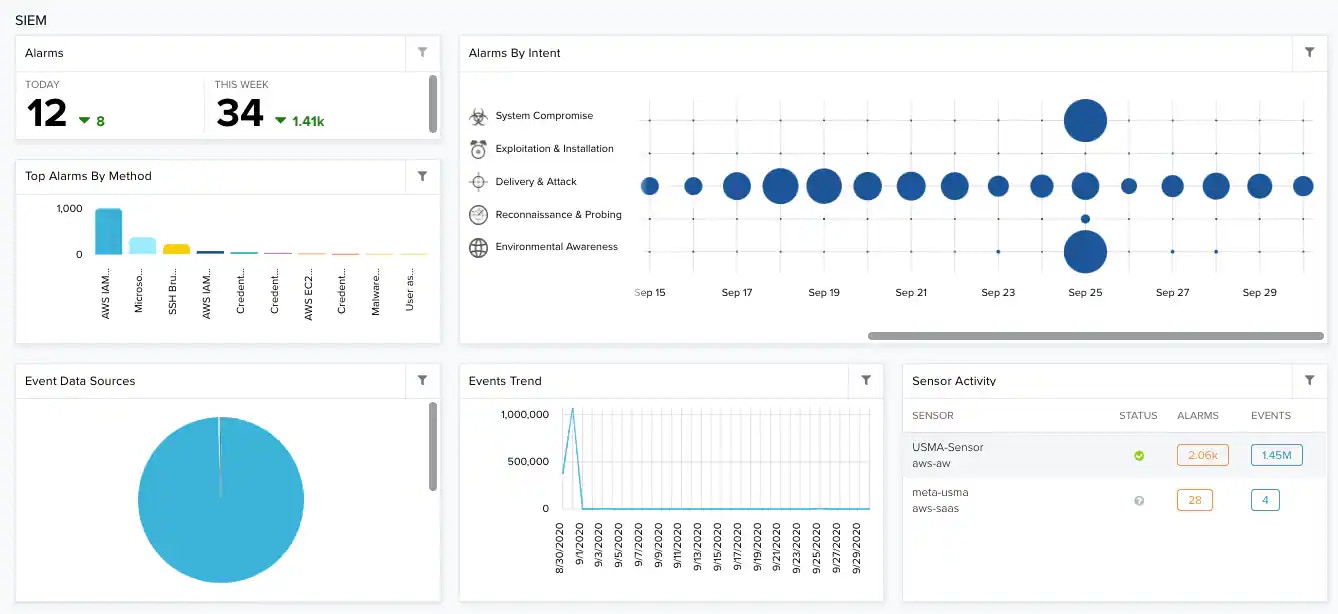
| Widget | Description |
|---|---|
| Total number of for the current day and for the current week. | |
| Alarms by Intent | Alarms correlated by intent and related to a range of dates. The size of the bubbles depends on the number of issues. |
| Top Alarms by Method | List of the top 5 alarms ordered by the method of attack or and including the total number of alarms. |
| Event Data Sources | Most seen data sources to normalize . |
| Events Trend | Graph that displays the trend in events. |
| Sensor Activity | Top activity by events and alarms. |
Asset Discovery Section
Discovery discovers assets in your environment, detects changes in assets, and discovers malicious assets in the network.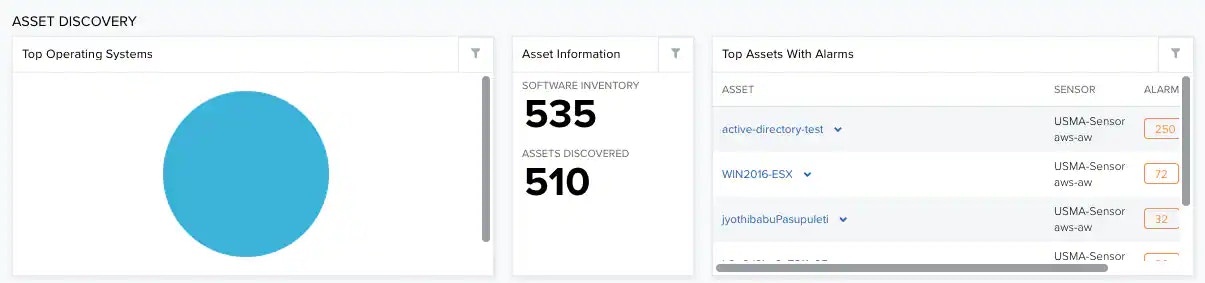
| Widget | Description |
|---|---|
| Top Operating Systems | List of the top on assets. |
| Asset Information | Software Inventory refers to the total number of assets having software installed. Assets Discovered refers to the total number of assets discovered by the user. |
| Top Assets with Alarms | List of the top 5 assets having the most alarms. |
Vulnerability Assessment Section
identify vulnerabilities or compliance by comparing the installed software on assets with a database of known vulnerabilities.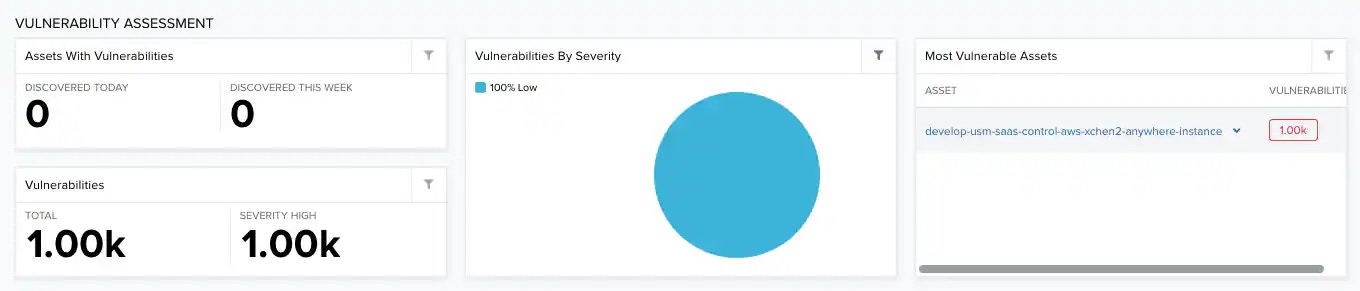
| Widget | Description |
|---|---|
| Assets with Vulnerabilities | Total number of assets having vulnerabilities for the current day and for the current week. |
| Vulnerabilities | Total number of vulnerabilities in your environment. |
| Vulnerabilities by Severity | Top vulnerabilities ordered by severity. See About Vulnerability Severity. |
| Most Vulnerable Assets | List of most vulnerable assets. |